New in Symfony 2.6: The security:check command
 Javier Eguiluz
Javier Eguiluz
Warning: This post is about an unsupported Symfony version. Some of this information may be out of date. Read the most recent Symfony Docs.
Contributed by
Fabien Potencier
in #149.
Symfony 2.6 is going to be one of our most polished releases ever. As part of the DX initiative we are tweaking and simplifying each and every part of the framework, from the installer to the error pages.
In addition to these improvements, we are introducing some new features that are
important for professional PHP development. One of those features is the new
security:check command, which looks for known security vulnerabilities
in your project's dependencies.
Using it is as simple as entering your project's directory and executing the following command:
1
$ php app/console security:checkThis command looks for the composer.lock file of your project. Then it
checks all the known vulnerabilities for the specific dependencies and versions
that your project is using. If no problems are detected, you'll see the
following message:
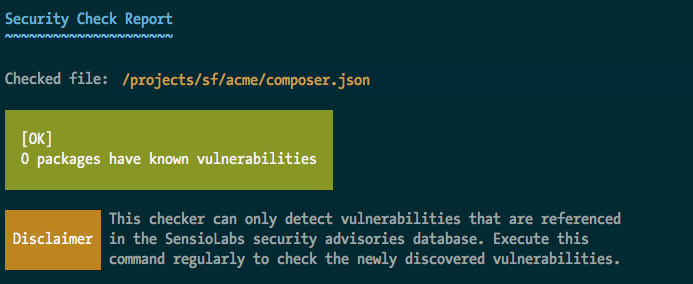
If there is any security problem with your dependencies, you'll see the following extended message which explains the exact vulnerability found for each dependency:
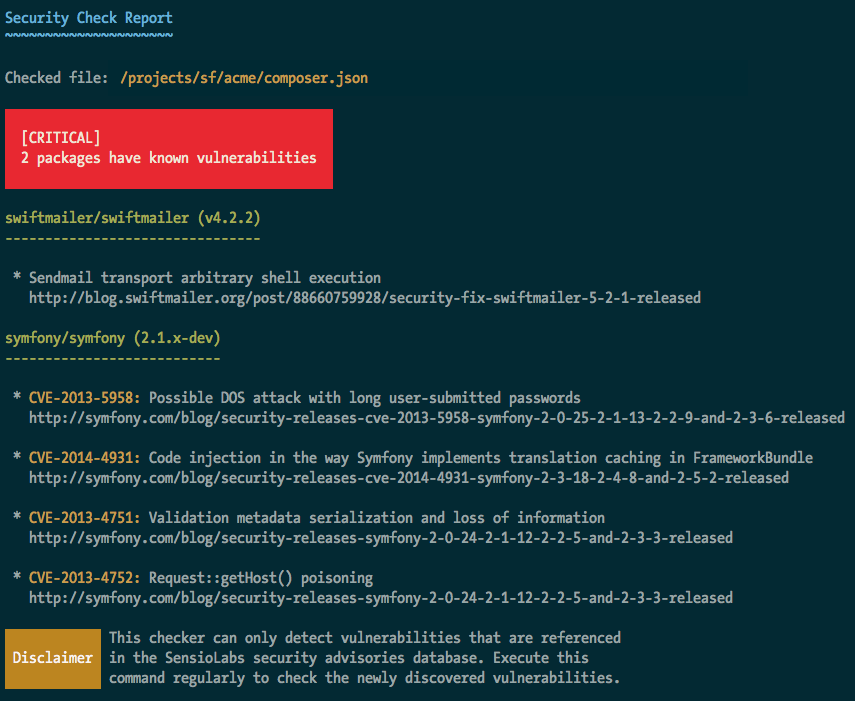
And for those of you with non-conventional project setups, the path for the
composer.lock file is configurable. Just provide the absolute path of the
file as the first argument of the command:
1
$ php app/console security:check /path/to/another/composer.lockInternally, this command uses the SensioLabs Security Advisories Checker and the public database of vulnerabilities for PHP projects and libraries. Both services are open to the whole PHP community, and we encourage you to contribute security advisories for your own projects.
Help the Symfony project!
As with any Open-Source project, contributing code or documentation is the most common way to help, but we also have a wide range of sponsoring opportunities.
Comments
Comments are closed.
To ensure that comments stay relevant, they are closed for old posts.
For Symfony 2.5 or lower you could use the standalone CLI checker from https://github.com/sensiolabs/security-checker.
Download the PHAR from http://get.sensiolabs.org/security-checker.phar and use:
$ php security-checker.phar security:check composer.lock
So, it should be cool to integrate this to the 2.7 branch.